OTHER HACKING TRICKS
May 09, 2018
Hack anyone's computer by sending Email - hackvak
 |
Hack computer by sending Email
Hay guys today i am gonna tell you how to hack a computer by sending email !
Using email is one of my favorite ways of breaking into an organization!
Usually, I will send out 10 emails to different employees. Out of those 10 people, 5 will click the link that I included. Of the 5 people, two or three will tell me their real work username and password. Pretty scary, isn't it?
Why are they so interested? Why would they give me their passwords? The email that I send does not look like a scam from a rich prince in an African nation. Instead, it looks like a professional email from a company conducting a survey on behalf of the employee’s organization.
Who wouldn’t be interested in filling out a survey about Salary Satisfaction?
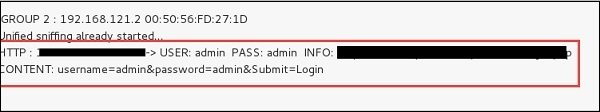
Once they click on the link, they are taken to a login page. It is then than an average of 25% of the people emailed submit their passwords.
This is where the fun begins!
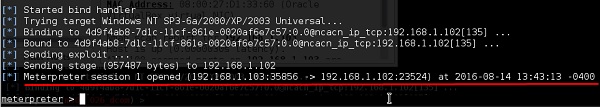
If the company is using Microsoft Exchange (email server), I can use their credentials to synchronize a copy of their email onto my computer.
Once it is synchronized, I can create a client-side rule that runs a program every time a certain email is received.
 |
This rule will synchronize over Exchange across all the computers that use that persons account.
Once they receive the special email, my program runs on the victim’s computer.
At this point, it is usually trivial to gain access to the rest of the network.
The other option is to send a user a malicious Word document. However, that usually requires building up a context where it would make sense for that attachment to be opened.
Recently, I received a very interesting attachment. It was an obvious attempt to break into my computer using a malicious Word document.
It came at a time where I was needing a more effective payload to send to my potential victims.
I was so greatful to the hacker for introducing me to a new technique that I replied with a thank you note.
The Word document contained an embedded object that appeared to be a another document. But in reality, it was a VB Script that would launch a malicious payload. Fascinating!